Auditing VSTS Client Access IPs

Visual Studio Team Services (VSTS) is a cloud platform. That means it’s publicly accessible from anywhere - at least, by default. However, Enterprises that are moving from TFS to VSTS may want to ensure that VSTS is only accessed from a corporate network or some white-list of IPs.
To enable conditional access to VSTS, you’ll have to have an Azure Active Directory (AAD) backed VSTS account. The conditional access is configured on AAD, not on VSTS itself, since that’s where the authentication is performed. For instructions on how to do this, read this MSDN article.
Audit Access
However, this may be a bit heavy-handed. Perhaps you just want to audit access that isn’t from a white-list of IPs, instead of blocking access totally. If you’re an administrator, you may have come across the Usage page in VSTS. To get there, navigate to the landing page for your VSTS account, click the gear icon and select Usage:
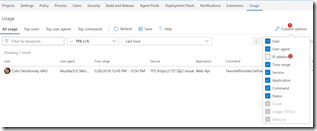
This page will show you all your access to VSTS. To see the IPs, you have to add the “IP Address” column in the column options:
Nice, but what about other users? To get that you have to use the VSTS REST API.
Dumping an Exception Report with PowerShell
There is an (undocumented) endpoint for accessing user access. It’s https://<your account>.visualstudio.com/_apis/Utilization/UsageSummary with a whole string of query parameters. And since it’s a REST call, you’ll need to be authenticated so you’ll have to supply a header with a base-64 encoded Personal Access Token (PAT).
Using PowerShell, you can make a call to the endpoint and then filter results where the IP is not in the white-list of IPs. Fortunately for you, I’ve made a gist for you, which you can access here. When you call the script, just pass in your account name, your PAT, the start and end date and the white-list of IPs. Any access from an IP not in this list is dumped to a CSV.
Limitations
There are some limitations to the API:
- You’ll need to be a Project Collection or Account admin to make this call (since there’s no documentation, I’m guessing here).
- You can only go back 28 days, so if you need this as an official exception report you’ll have to schedule the run.
Conclusion
VSTS knows the client IP for any access. Using the API, you can dump a list of access events that are not from a white-list of IPs.
Happy auditing!